A quick guide to encrypted messaging Encryption stormagic Encryption types symmetric asymmetric hash algorithm aes key vs algorithms hashing encoding project security computer obfuscation cryptography pki data example
A Quick Guide to Encrypted Messaging | Network Wrangler – Tech Blog
Encryption key public usb works oracle drive explained software flash figure lock ophtek gif need do drives server implementation basic
Transit encryption
Encryption decryption encrypted encrypt decrypt hashing ciphertext salting cloudsoft zone frameworks wondering accounts examinationsEncryption infographic messaging secure encrypted cyberwarfare cybersecurity Encryption wired retain storing private explainedWhat is encryption and do you need it?.
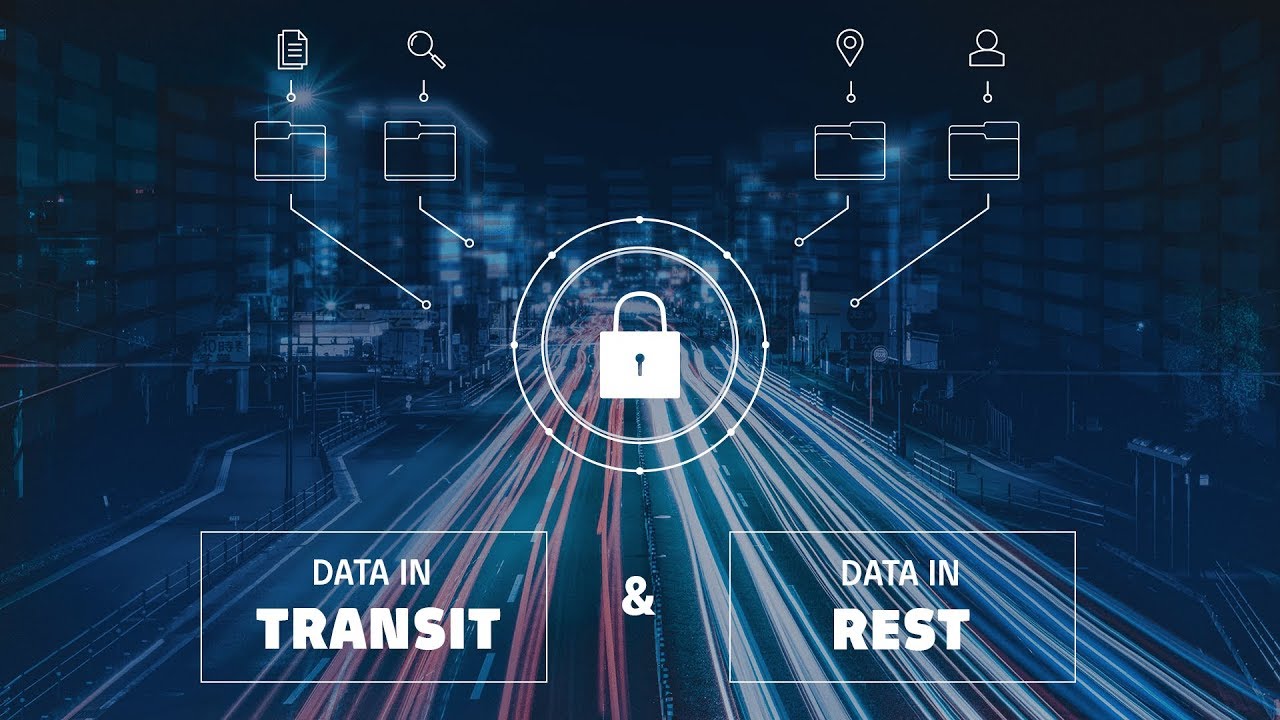
Encryption: what is it and how does encryption software work?How does https work? rsa encryption explained « tiptopsecurity What does encryption of data-in-transit and data at rest mean?Encryption hashing okta definitions.

Encryption ssl work explained use does rsa data protocol web secure website server certificates hackers encrypt tips wordpress version illustration
Advantages and disadvantages of pgp encryptionEncryption asymmetric does work data example works decryption use algorithms keys plaintext changes symmetric Pgp encryption hashing usemynotesHashing vs. encryption: definitions & differences.
What is encryption and how does it work? .